
August 20th 2025 Meetup
The BurntToast PowerShell module is like a personal chef for your Windows notifications — it serves up those little pop-up messages in the corner of your screen, but with way more flavor.
Read More
The BurntToast PowerShell module is like a personal chef for your Windows notifications — it serves up those little pop-up messages in the corner of your screen, but with way more flavor.
Read More
Jake Hildreth will join us to show how he used Crescendo to turn those clunky CertUtil.exe commands into smooth, PowerShell-friendly tools you’ll actually enjoy using.
Read More
PowerShell is such a capable and versatile tool that the advice we sometimes hear is to replace the question “Can you use PowerShell to do that?” with “Should you use PowerShell to do that?”.
Join Lucas Allman as he explains how he ignored that advice completely and built a Configuration as Code (CaC) toolset in PowerShell for managing his team’s device management and reporting automations.
Read More
Join Anthony Howell, @theposhwolf, for an insightful session exploring the power of hash tables and PS custom objects in PowerShell. Whether you’re managing large datasets, optimizing script performance, or presenting clean, structured output, this session will provide a comprehensive look at when and how to use these tools effectively. Anthony blends technical expertise with humor, making complex topics accessible and engaging for all skill levels.
Read More
Get ready to explore the incredible tiPS module with Dan Schroeder, designed to deliver valuable tips and tricks directly in your PowerShell terminal shell.
Read More
Join Thomas Nieto as he introduces his module, AnyPackage! With this powerful tool, you can easily install software packages from popular repositories using just one set of cmdlets.
Read More
🌟 Calling all coders! 🖥️ Join us for a fun community event where you can show off your PowerShell coding skills in quick 5-10 minute demos. Whether you’re a newbie or a pro, everyone is welcome to share their tools and scripts.
Read More
Let’s check out PowerShell Universal and explore what’s new in version 5, set to launch in the next few weeks!
Read More
Join us this month for PowerShell learning with demo from Phil Bossman.
Read More
Join us this month for twice the PowerShell learning with demos by Mike Kanakos and Phil Bossman.
Read More
Join Joe Houghes for an overview of best practices you should follow for open source projects. We’ll discuss source control, collaboration, and managing coding environments for coding and automated testing.
Read More
Ever needed to perform the same work against multiple instances of SQL Server?
Read More
🌟 Calling all coders! 🖥️ Join us for a fun community event where you can show off your PowerShell coding skills in quick 5-10 minute demos. Whether you’re a newbie or a pro, everyone is welcome to share their tools and scripts.
Read More
Join Josh Hendricks for a look at how build functional AND beautiful documentation from your existing code with PlatyPS.
Read More
Join PowerShell veteran Jeffrey Hicks for a primer on how to write better scripts and take your code to the next level!
Read More
Join us as we explore AutomatedLab, a powerful PowerShell module that helps create virtual lab environments for testing.
Read More
Make the transition from Windows Server Pro to Linux Server Ninja by using PowerShell to your advantage!
Read More
“How do I build a GUI using PowerShell ?” Join Kevin Laux for a crash course on what’s available and how to get started
Read More
Join James Brundage and discover how to unleash the full potential of PowerShell with PipeScript!
Read More
What happens when you blend SNMP and PowerShell together? Primarily, you end up with a headache and a broken blender.
However, it can also be an enjoyable experience when you uncover the hidden data points that have been right in front of you all along. Impress your bosses with visually appealing charts, provide solid justification for equipment upgrades, and enhance observability.
Read More
Learn PowerShell security fundamentals and best practices to safeguard your scripting environment.
Read More
Join us for another RTPSUG PowerShell Skill Builder session. This month we’re covering the essentials of searching Active Directory and creating useful reports!
What are PowerShell Skill Builders? The concept behind this series is simple - we’re here to tackle everyday problems as a group. And guess what? There’s more than one way to solve these challenges!
Many of you will have your own tricks up your sleeves, and the paths you take to find the answers can be quite diverse. By peeking into the methods your teammates use, we can all pick up some fresh problem-solving skills. So, get ready to learn together and have some fun while you’re at it!
Read More
Learn how to create a single profile script that can be used for all PowerShell versions and across multiple operating systems.
Read More
Get ready to dive into the world of data formatting for all your reports and outputs, alongside your fellow RTPSUG group members!
We’re excited to kick off our new series: “PowerShell Skill Builders!”
Read More
Join us to gain valuable insights into the PowerShell Application Deployment Toolkit (PSADT) and its capabilities for optimizing application deployment workflows. We’ll explore the practical applications deployments, custom extension functions, and other automation strategies in PSADT, all aimed at empowering and streamlining your deployment processes.
Read More
Creating and managing a blog can be a formidable task, demanding substantial time and effort. However, the adoption of #PowerShell and automation offers a great solution to this challenge.
Read More
When you find a PowerShell script online to address an issue, it often doesn’t meet all your needs. You’ll usually have to customize and tailor the script to suit your specific requirements. Join us to learn techniques for making it your own.
Read More
Becoming a seasoned PowerShell professional is not an overnight achievement. Learn about the parallels between the journey of preparing for a marathon and mastering any skill, with a particular focus on PowerShell.
Read More
Monica Albuerne joins us to talk about common resume mistakes that hurt you when it comes time to negotiate compensation. After our demo, we’ll host an open forum to talk all things PowerShell.
This is a hybrid event. You can attend in-person or online via Microsoft Teams. See below for important details for attending in-person.
Read More
They say that you learn far more by doing than by just listening…. Join Devin Rich as he takes you on a hands-on, guided tour of working with APIs in PowerShell.
Read More
Adam Driscoll @adamdriscoll joins us to walk through all the cool things that you can with PowerShell Universal)!
Read More
Joel Bennett @Jaykul will chat with us about how to get started with extensible module authoring, and making your PowerShell session pretty.
Read More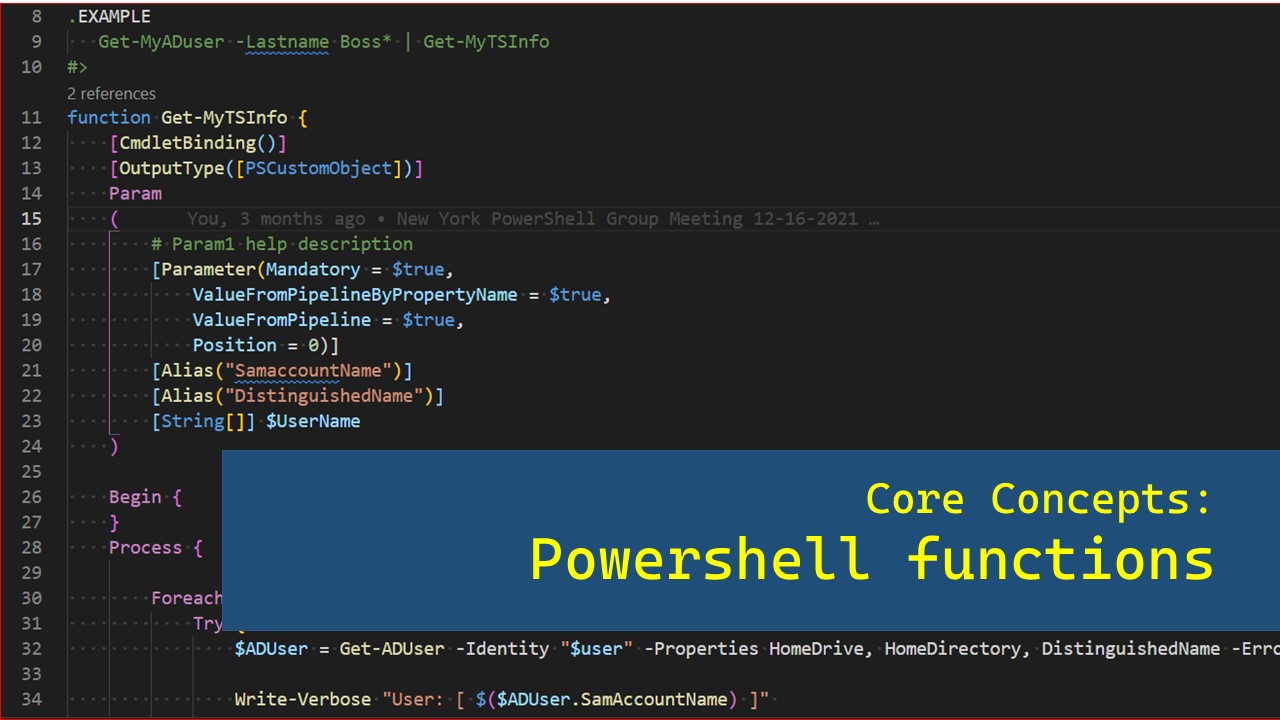
Come and walk through building your first function. We’ll discuss the parts of a function, how to use them, and ways to effectively use functions to accomplish your goals. We’ll also discuss creating Advanced Functions and how they can improve your scripts.
Read More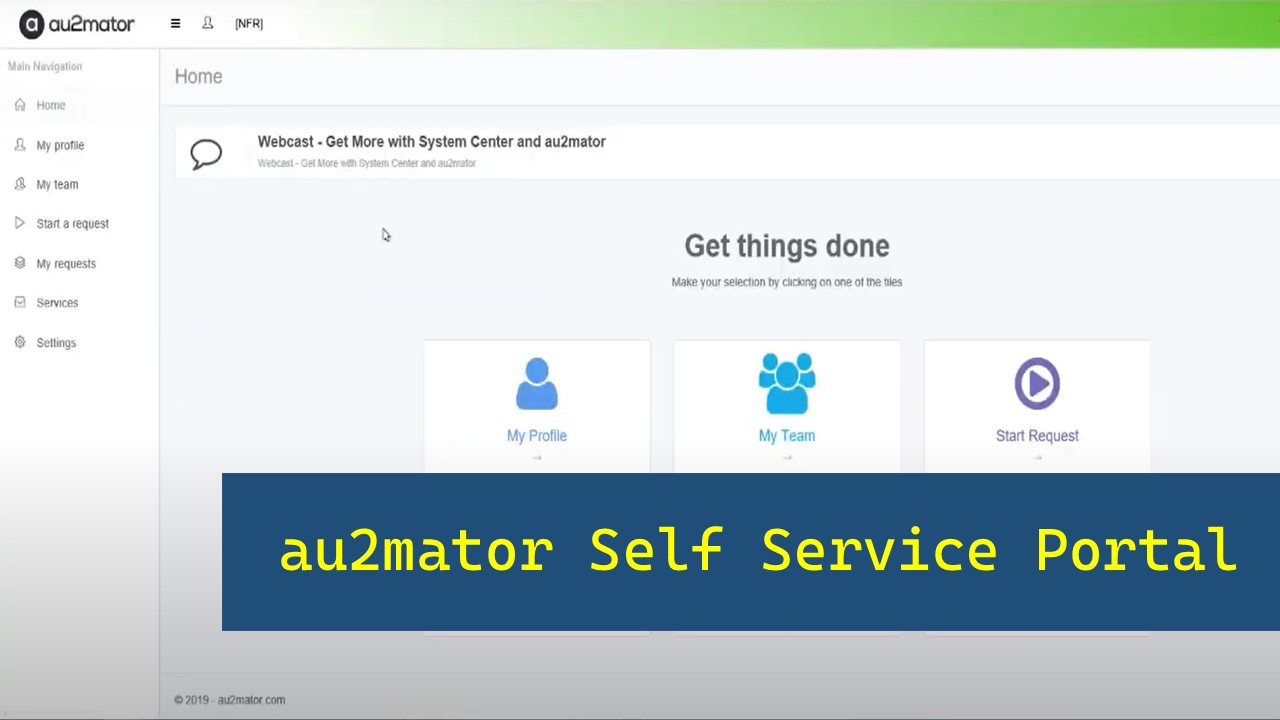
Get the most out of Microsoft Automation with au2mator Self Service Portal. You can use PowerShell, Azure Automation, or System Center Orchestrator to delegate your Automation Tasks.
Read More
Microsoft has stated the AzureAD and MSOL modules are being deprecated! We need to move to the Microsoft.Graph module if we want our scripts to keep working. Come join us to see how to get started with the Microsoft.Graph module. We’re going to look at how to explore the Graph module, use it interactively, setup an app registration for automation, create some users and groups, and pull back some information about those objects.
Read More
PowerShell v7.2 is now a GA release. See what new features are available and how you can customize the screen prompts with the new variable that contains ANSI terminal colors.”
Read More
Join Bradley Wyatt @Bwya77 for a look at how he build the PSWordle game and you can get started building your own version.
Read More
This presentation, we welcome Anthony Howell @ThePoshWolf. Anthony will showcase the usage of the free community version of Runway Automation Platform
Join Anthony as he talks about Runway and focus on the cool parts of scripting with Runway. They are looking for testers, so get ready.
Read More
Time for the community to roll their sleeves and show off their own code in small 5-10 minute demos. Let’s share the tools and scripts that we use in our daily work lives. Anyone can share: beginner to advanced!
Did you solve a problem at work that you think could help someone else? Share your knowledge and pass along some tips and tricks to fellow community members.
Read More
This presentation will primarily showcase usage of the PowerShell module TrackGpo, how it can tie in to Git repos, and how to extend its functionality. TrackGPO is a PowerShell module that allows you to track changes to Group Policy Objects (GPOs) easily.
Join Devin as he talks about challenges that he faced while turning group policy into a predictable and usable set of data!
Read More
Let’s talk about how we can take automation beyond the infrastructure IT role, and show how it can be used to automate the process of upgrading server-based applications. We’ll cover taking snapshots in vCenter, disabling server monitoring, stopping services on multiple servers, terminating file share access, resetting IIS, modifying config files, and cleaning up; all from a single server.
Read More
This past week I needed to find duplicate links across nested OUs within my org. The suspicion was there were a lot of GPOs linked repeatedly that could have been linked once at a higher level. I thought I might make a quick post to talk about how I got the information. Along the way, we can learn a little about Active Directory and GPOs.
GPOs, otherwise known as Group Policy Objects, apply desired state to domain joined devices and users. Each Group policy consists of a Group Policy Object and Group Policy Template. Every Group Policy you make can apply to a user, computer, or both. When you make a GPO, the template contains a ‘.POL’ file that imposes the desired state. The .POL file is deployed from SYSVOL. To go along with the template, there is an object that exists within the Active Directory database. The object maintains consistency with everywhere an admin links a Group Policy. That means if I have one Group Policy linked to 3 different OUs in the domain, I have one template and three references to that Group Policy Object.
If you have the ActiveDirectory RSAT installed, you will have a few PowerShell modules installed on that device. Not only do you get the ActiveDirectory module, you also get a GroupPolicy module. We can look at what commands are available in the GroupPolicy module with:
Get-Command -Module GroupPolicy
Here we can see a lot of opportunity to interact with Group Policy; however, most of the options work on the template. What we’re interested in is the object. These cmdlets allow the ability to create a new GPLink, which would affect a Group Policy object in AD. But how can we count where a single GPO is linked everywhere in the domain?
Here is the script. In this script we’ll take in a DistinguishedName of an Organizational Unit and look for all GPOs linked from that location and further down the tree. We’ll start by getting a list of OUs to search across by issuing:
$OuTree = Get-ADOrganizationalUnit -Filter * -SearchBase $SearchBaseDn -SearchScope Subtree
Next, we need to evaluate the Group Policy GUID stored in AD against a friendly name. To do this, we need to get all the GPOs in the domain. We’ll grab those with this command.
$AllGPOs = Get-GPO -All
If we look at a single OU, we can see there is a LinkedGroupPolicyObjects attribute.
This is what we’re after.
This property will hold a list of all the GPO GUIDs linked at that OU.
Once we have those GUIDs, we can do a lookup against our list of all the GPOs and return a friendly name.
To accomplish this, I created a couple of private functions to help with the work.
The first private function looks like this:
function GetGpoGuids {
param (
$LinkedGpos
)
$RegexPattern = '[A-Z0-9]{8}-[A-Z0-9]{4}-[A-Z0-9]{4}-[A-Z0-9]{4}-[A-Z0-9]{12}'
foreach ($ou in $LinkedGpos) {
($ou | Select-String $RegexPattern).Matches.Value
}
}
In this function, we can take the list of Group Policy links and retrieve just the GUID for that GPO.
Since the LinkedGroupPolicyObjects attribute is going to contain a list of items that look something like this:
cn={316E23FF-9546-46BB-AB06-729FF2058E36},cn=policies,cn=system,DC=your,DC=domain,DC=com
This code will use the regex to strip away everything but the GUID inside the curly braces and return only that as a value.
316E23FF-9546-46BB-AB06-729FF2058E36
Furthermore, since an OU may have more than one Group Policy linked to it, the attribute may have more more than 1 Group Policy link referenced.
We can just pass all the values in the list, whether that’s 0 or 100, through a foreach loop and output all the GUIDs.
The next private function looks like this:
function GetGpoFromGuid {
param (
$GpoGuid
,
$GpoSearchBank
)
$GpoSearchBank.Where({$_.Id -eq $GpoGuid})
}
This function will take care of the lookup. Here we will take in two parameters. The first is the GUID of a single GPO link on an OU. The second is the list of Group Policy objects we retrieved earlier. From there, we can take the comprehensive list of all the GPOs and filter it down to a single GPO by looking for a matching GUID. We’ll use that output, the entire GPO, in the main script.
Now that we have looked at the private functions, let’s look at the main script.
foreach ($ou in $OuTree) {
$LinkedGpos = $ou.LinkedGroupPolicyObjects
$GpoGuids = GetGpoGuids -LinkedGpos $LinkedGpos
$Gpos = $GpoGuids | ForEach-Object {GetGpoFromGuid -GpoGuid $_ -GpoSearchBank $AllGPOs}
foreach ($gpo in $Gpos) {
$Result = [PSCustomObject]@{
OuName = $ou.Name
OuDN = $ou.DistinguishedName
GpoName = $gpo.DisplayName
}
$Result
}
}
The working code is quite short. We’ll take each OU, evaluate it to retrieve the list of GUIDs for all linked GPOs, and return a custom object. The custom object will contain the DN of the OU, the friendly name of the OU, and the friendly name of the GPO. From here, we can store this in a variable and work on exploring afterward. Once I completed the script, I quickly executed the following code from my terminal:
$GpoInfo = .\Get-GpoByOu.ps1 -SearchBaseDn 'OU=foo,DC=domain,DC=com'
$GpoInfo | Export-CSV -Path 'GpoByOu.csv'
Following that, I could start counting duplication by using Group-Object
$GpoInfo | Group-Object GpoName | Sort-Object Count -Descending
This would give us a count of how many links each GPO has per the OUs in the tree.
Read More
Ansible is an amazingly flexible tool to manage your infrastructure. Jeremy Murrah @JeremyMurrah will be showing how you can get started using ansible to manage Windows Servers and treat your servers as “cattle” and not “pets”.
Read More
PowerShell has surpassed the administrative use that it was originally developed for and now additionally serves as a capability that enables threat hunters and incident responders to illuminate malicious activity and respond to such threats.
Read More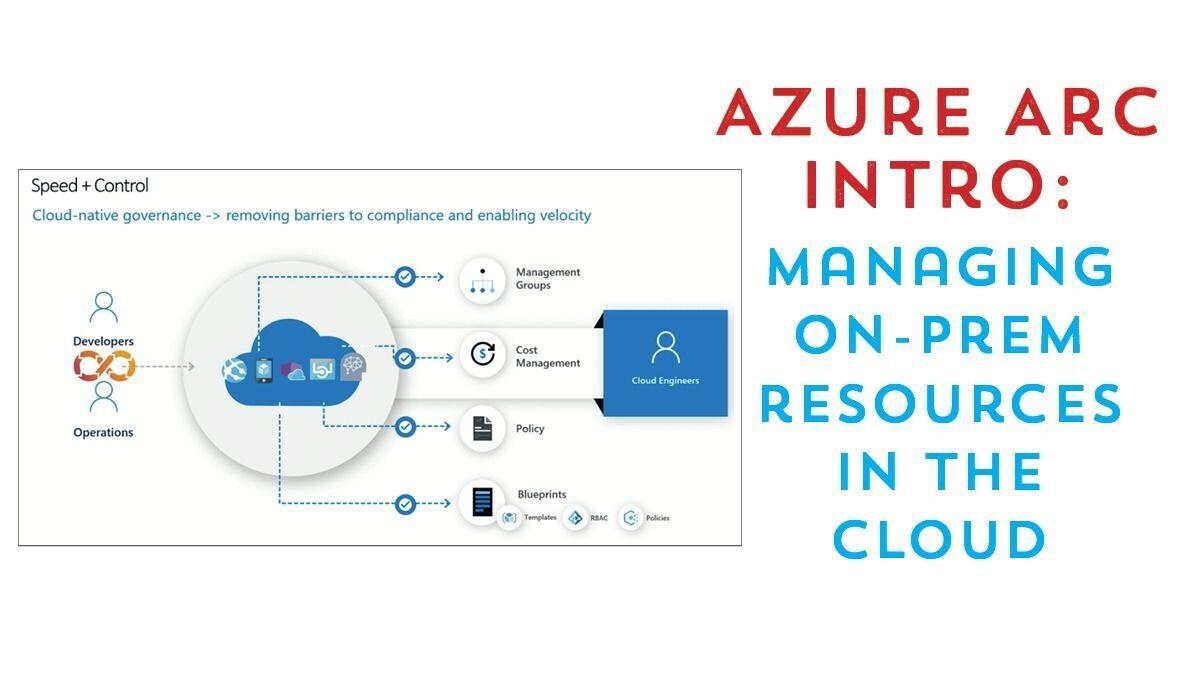
You’ve might have heard the news about Azure Arc and how it enables multi-cloud management from Azure. However, there’s a secret that not many people know… you can manage your on-prem resources with Azure Arc.
Read More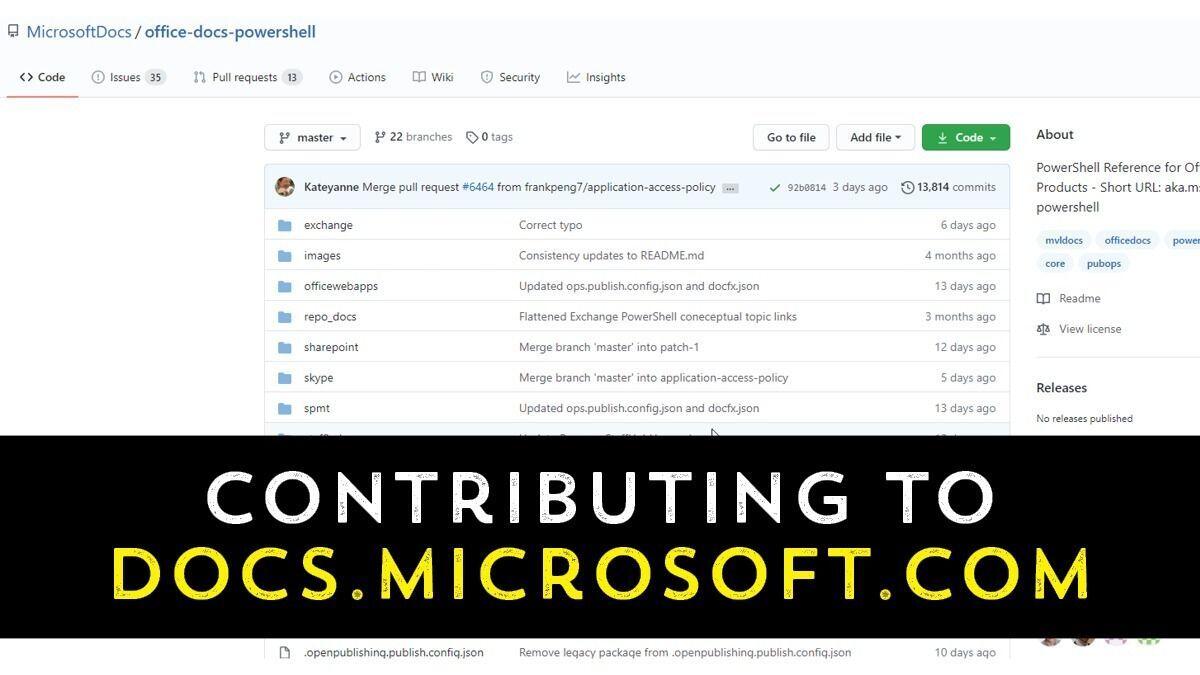
docs.microsoft.com is the home for Microsoft documentation. It is a valuable resource for IT pros to learn how various Microsoft services and products work. What may not be well-known is that the docs website is open source! Anyone can contribute, edit, change, add to the documentation available. The question is how to does someone make a change and what happens after they submit a change?
Read More
Working with code in Git repositories is a required skills now for most IT pros. But if all you do with Git is add, commit, push, and merge, then you’re missing out on a world of functionality. There are so many opportunities to customize Git to increase productivity and automate CI/CD related actions. It’s time to unlock the phenomenal power of Git hooks and put Git to work!
Read More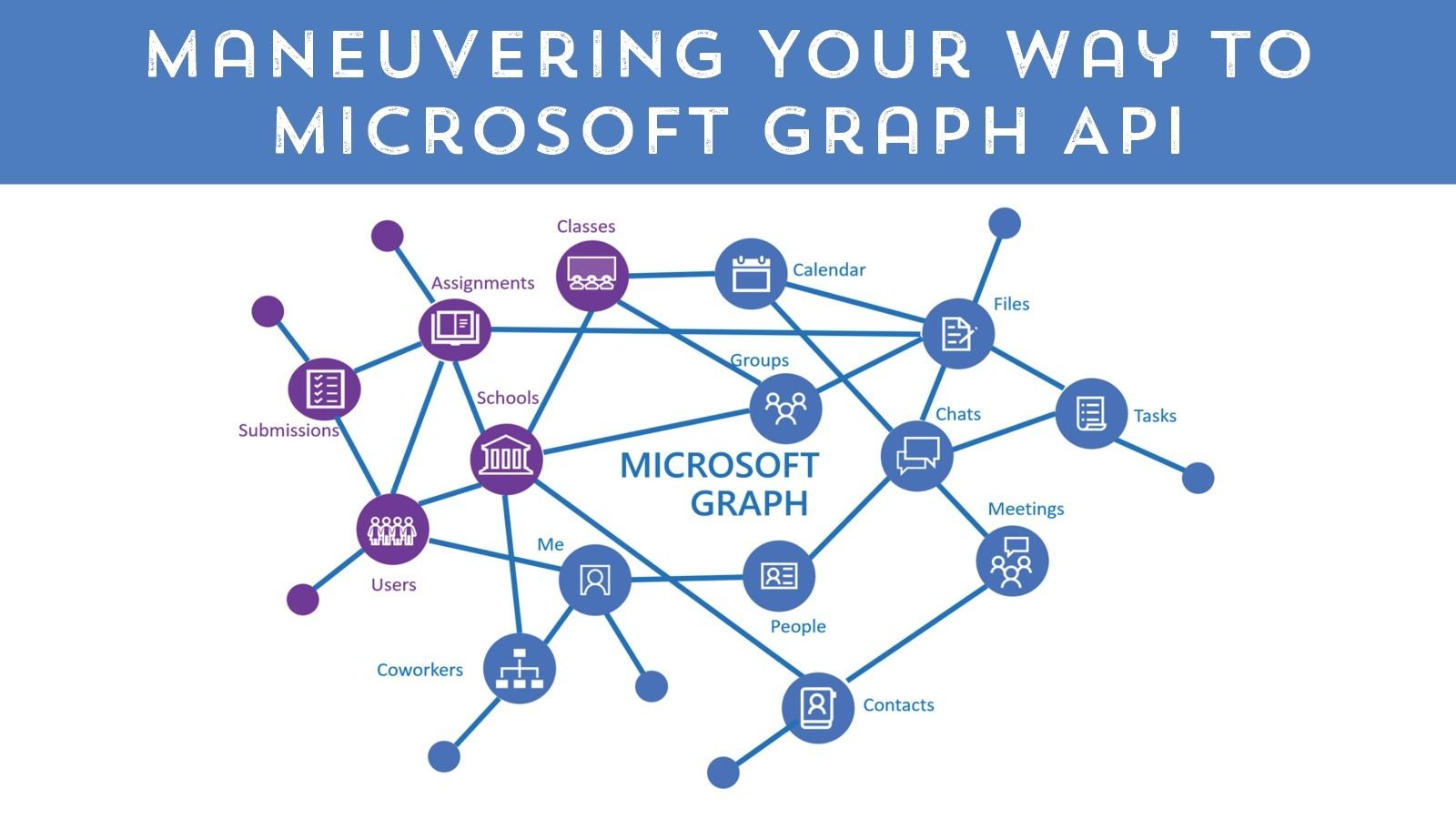
The Azure cloud is a nearly limitless place to store data, host applications and perform complex calculations on your data. The method for accessing Azure cloud resources programmatically is the Graph API. Microsoft Graph is a RESTful web API that enables you to access Microsoft Cloud service resources.
Read More
Sadly, PowerShell + DevOps Global Summit 2020 had to be cancelled, keynote presenter Don Jones spent all that time working on his speech that it seemed a shame to waste it! So join in for… “You’re More Than Just a Scripter!”
Read More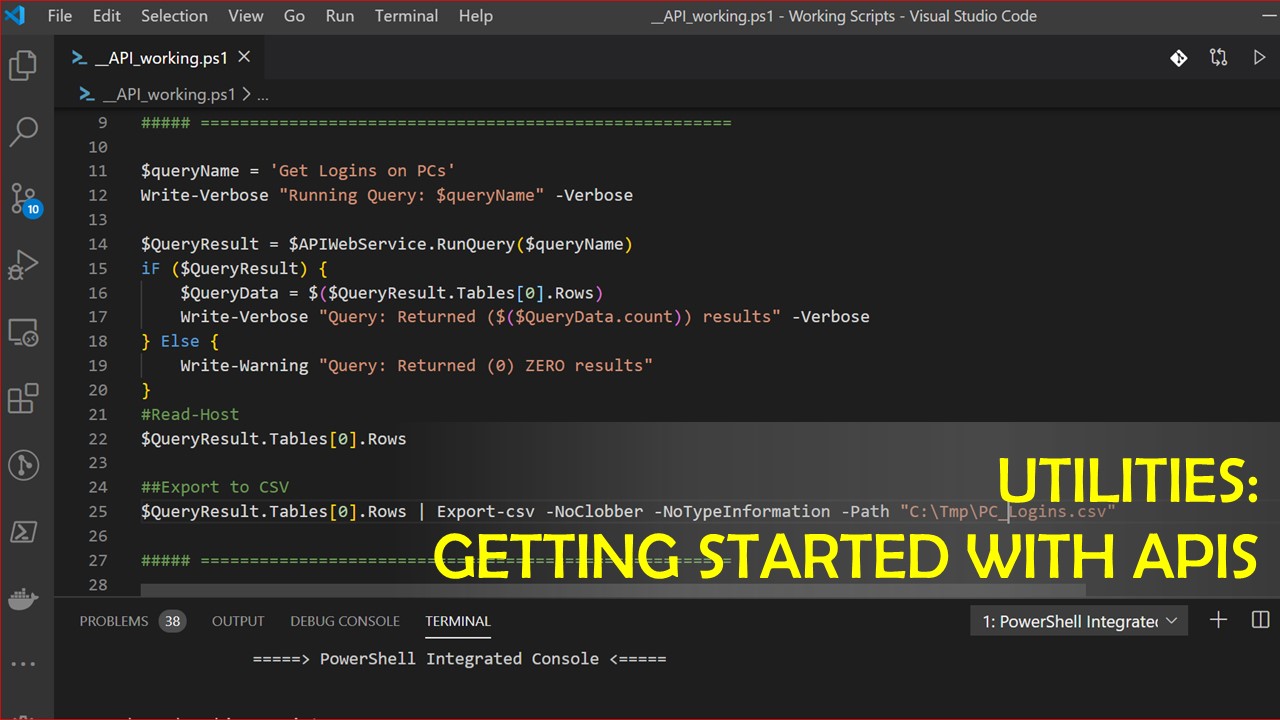
In today’s world of connected computers, using PowerShell is not limited to managing only your computer or the others on your network. It is possible to manage computers across the globe and consume information from the internet all from your PowerShell cmd prompt.
Read More
Join us as we lighten things up with April Fools Day fun and PowerShell tips and tricks!
Read More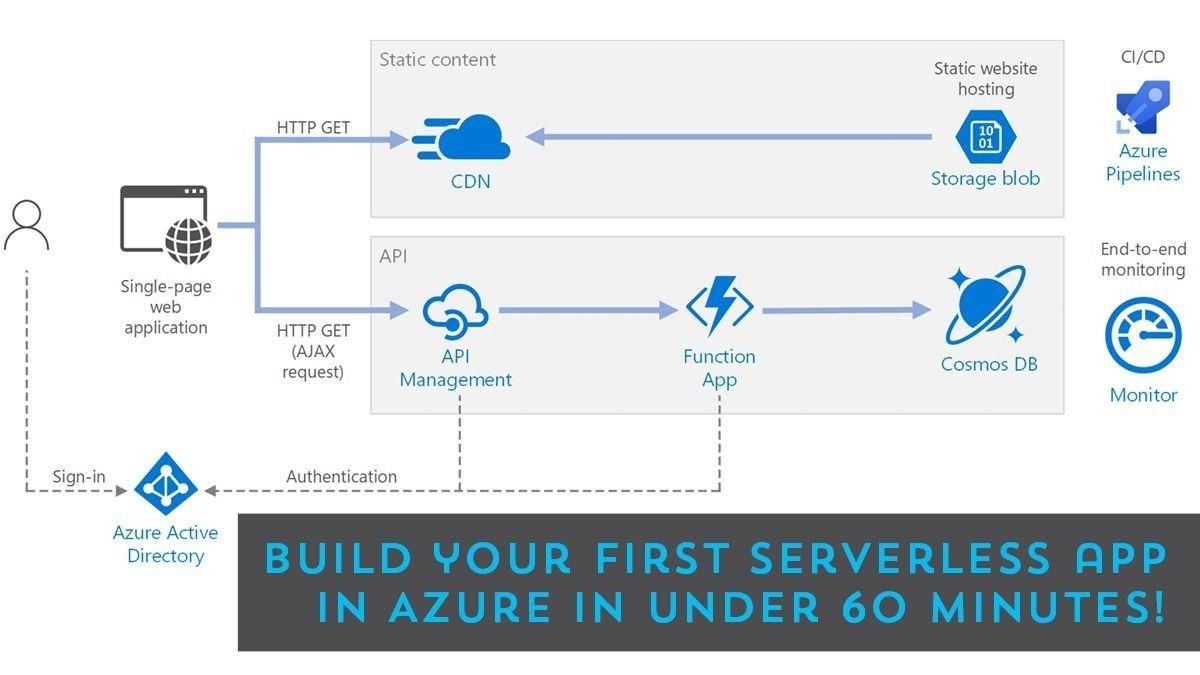
Looking to learn how to get started in Azure? Have you considered Serverless apps? Be not afraid. They’re easy to build and allow you get started without needing a degree in programming… .
Read More
It’s an exciting time in the world of PowerShell. Microsoft is about to release the next release of PowerShell to the general public any day now. This new release, known as PowerShell 7, brings with it many new tools and capabilities to help sysadmins, software devs and other IT pros.
Read More
We’re continuing our git education series with a follow up on last month’s git intro. Last month we focused on committing code to your own repo. This month we’re focusing on committing code to a shared repository.
Read More
This month we’re discussing one of the most useful tools in the PowerShell toolset: Hashtables. Our speaker this month is Microsoft MVP and PowerShell community hero Kevin Marquette.
Read More
If you have played with code at all you have probably heard about git. But what if you have no idea what git is or how to get started? This session is for you…
Join Phil Bossman and the rest of the RTPSUG leaders as we host the first of two hands-on, interactive git learning sessions. You will participate in follow-along demos to create and commit to your first repo. The RTPSUG leaders will help you master your first steps in git with one-on-one help.
Read More
Command-line utilities are great. But they don’t follow PowerShell patterns. They don’t produce objects and they don’t support the pipeline. They output to the console and that’s the end of the line. Or is it? Learn how you can bring the benefits of PowerShell to your command-line utilities.
Read More
REGEX!!! It’s often misunderstood and hated by many! But the truth is regex is super powerful and sometime it’s the best tool for the job!
Ever wish you could learn Regex in a simple, straightforward tutorial with one of the best speakers in the PowerShell community?
Read More
What’s in your profile script? What do you find useful to have auto-loaded for you when you start a PowerShell session?

Mike Kanakos will walk us through the major pieces of PowerShell remoting. This talk will focus on security and logging along with a discussion about convincing your InfoSec team that remoting is safe to use.
Read More
Jeremy Smith will present his talk he shared at PowerShell Saturday in Raleigh. He’ll be showing how custom formats can help make life easier for repetitive tasks.
Read More
Join us as we take a break from code and sit down with three industry veterans to discuss how PowerShell has played a role in their careers and where they see the industry headed - not just for PowerShell and automation - but for all of IT!
Read More
Please join us for a very special event!!!! Please be aware that this event will be held on a MONDAY NIGHT!!!
This month we are proud to be hosting Matthais Jessen in person to do a deep dive exploration of the corners of Active Directory Domain Services most admins probably don’t think about that often.
Read More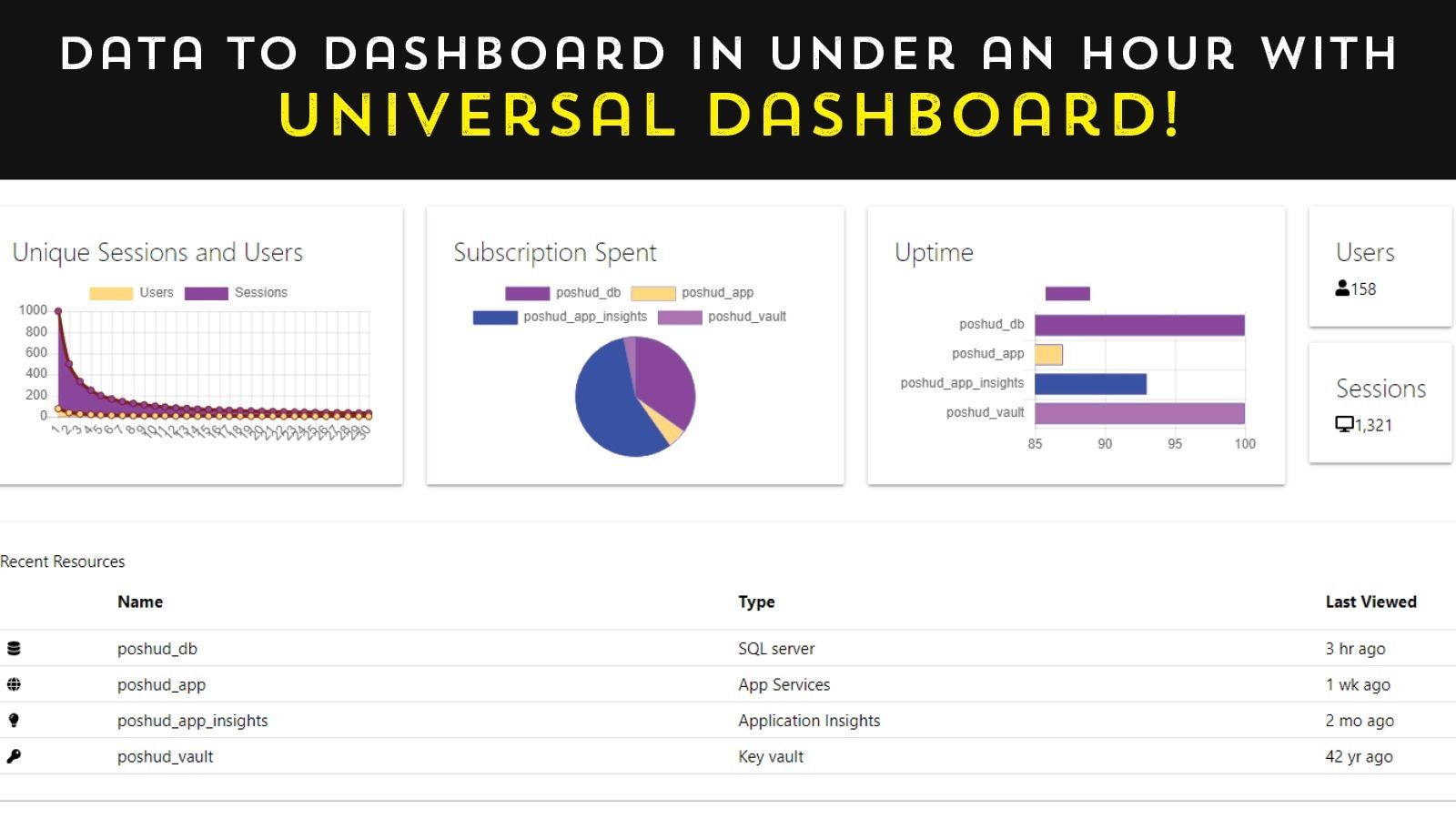
You’ve seen those eye-catching dashboards all over the web. They look super slick and really useful. How do they create them?
In this session, we’re going to introduce you to one of the slickest tools available for PowerShell: the Universal Dashboard module!! Our guest for the evening is Adam Driscoll, a software architect, business owner, and Cloud/Datacenter MVP. He is also a published author, open-source contributor, and speaker!
Read More
Are you confused about the differences between PowerShell and PowerShell core? Have you heard that PowerShell 7 is coming soon? Are you curious about how to run the different flavors of PowerShell side by side? What about remotely managing Linux/Windows hosts?
Read More
One of the great things about PowerShell is the barrier to entry is low. Writing simple scripts is a task that anyone can do with just a little bit of practice. The downside is that over time, many admins end up with a pile of half-baked scripts that don’t age well.
Read More
David Stein will be joining us this month to discuss how code and more specifically, PowerShell has become a tool he uses to to help meet customers demands and solve problems. He will be sharing with us specific examples of how PowerShell was able to find very specific data that customers wanted to find but did not have the tools or knowledge on how to get answers they need.
Read More
This meeting is about community and our awesome members! We’re opening the floor to our membership to share knowledge first-hand with one another.
Read More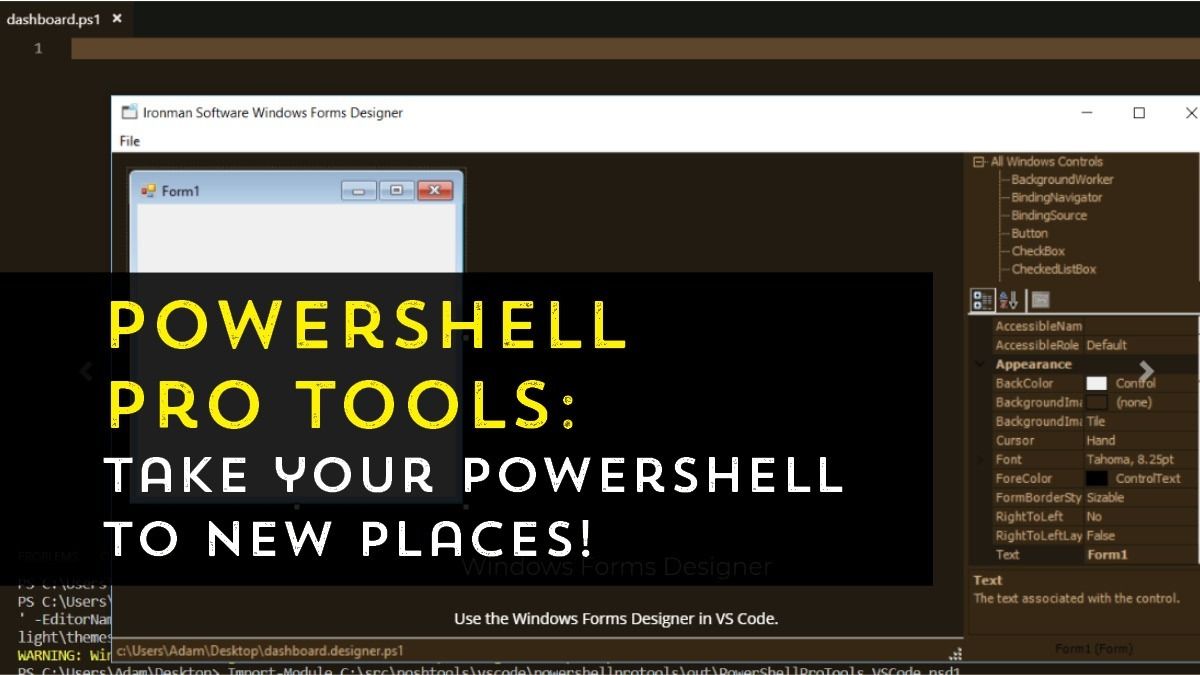
One of the greatest strengths of the PowerShell language is its flexibility. However, even though PowerShell is super adaptable, some tasks are still a challenge. Tasks such as creating a GUI front-end for your PowerShell function or packaging your PowerShell module as an EXE or DLL are not trivial tasks. That’s where 3rd party tools and add-ons can bridge the gap!
Read More
This is a new idea we’re looking to develop further and welcome your feedback on what you think of the newsletter concept for our user group. We are planning to send out a monthly newsletter that talks about all things PowerShell in the community and the things we have planned for the near future as well as a discussion of the topics recently discussed at groups meetings. We hope you find the information in our newsletter helpful and insightful. We’re still figuring out the right length, so please let us know what you think!
Read More
PowerShell has been responsible for introducing countless numbers of engineers to automation. Now come see how Chocolatey does the same for software distribution. The days of building complex multi-step MSI’s and zip installs are gone and in its place is simple to build and simple to install packages that can be run from a PowerShell command prompt with ease.
Read More
What’s the #1 request that we get at our user group meetings?
“What do you recommend for learning PowerShell?”
Of course, there is no right answer for everyone but this month we’ll be sharing with you an absolutely awesome way to learn PowerShell through an interactive PowerShell session!
Read More
Pester is a test framework for PowerShell. It allows you to define all kinds of test cases and report the results. Using this framework, you can build tests to automatically test every piece of code before it is released to production environments. The tests are limited mostly by your imagination!
Read More
The Research Triangle PowerShell users group has got a lot of great things planned for the coming months. See you Soon!
Read More
Most admins don’t have the time to keep an eye on every part of their IT infrastructure, let alone every nook and cranny of Active Directory.
Read More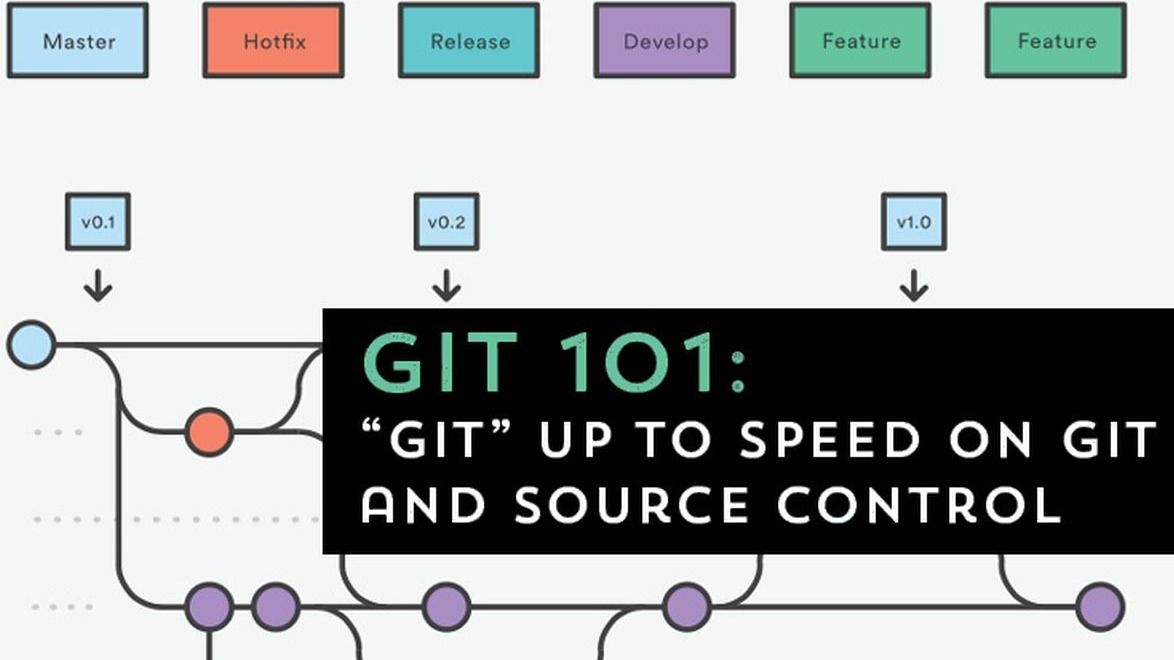
GitHub, GitLab, Bitbucket, Visual Studio Team Svcs, Azure Devops… all these tools for saving code work via the same basic backend language: git!
Read More
Giving everyone local administrator or domain administrator privileges is a really bad idea. Even the best of admins can make mistakes which can have unexpected consequences.
Read More